Phishing Emails and How to Protect Yourself

We have seen a significant increase in the volume of Phishing emails being sent globally. The trend is expected to rise and users should be prepared and educated on how to identify emails from what is legitimate or not.
Phishing emails usually contains malicious attachments and suspicious web links in the body of the message.
We have no direct control over attackers from sending out Phishing emails. But we can help prevent ourselves from getting victimized by learning how Phishing works.
Typical example of a Phishing email
Scenario:
Jim and Joyce had known each other for a long time.
They work on the same company, Hawkins National Laboratory. They both use their provided company email addresses to exchange emails. The email addresses follow the format “firstname@hawkinslab.com”.
One day, Jim received an email from “Joyce” asking for payment details.
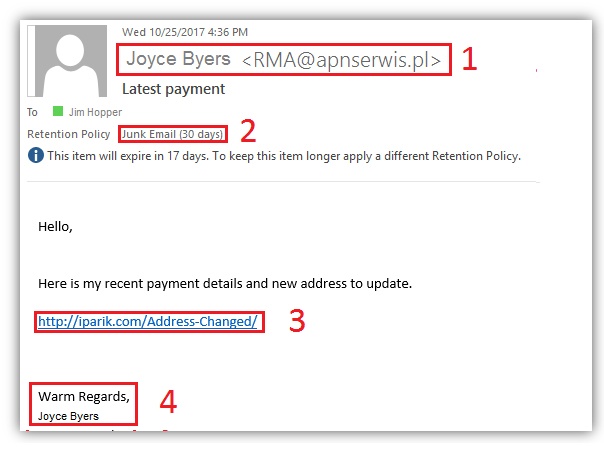
From the image above, the email has been flagged FOUR times.
The SENDER, Joyce obviously didn’t use her Company EMAIL.
![]()
Look closely. The email used Joyce Byers as the display name. But the email address beside her name shows something else.
Outlook correctly identified the email as JUNK.
![]()
From this point on, we should already know that this was a Phishing email. Let us continue with the rest of the message in cases where it was not flagged as Junk.
There is a link in the BODY asking you to click and open from your web browser.
![]()
This link will lead you to a FAKE website or download a malicious file on your computer.
NEVER click any of the links within the email!
There is also a note saying not to reply to that email. Replying will increase your chances of getting scammed or the email will simply bounce back because that is not a valid email address.
To make it look believable, the Phishing attacker includes a signature at the bottom. Do not click this as well. This is all part of the plan to make you believe that the email was legitimate.
![]()
In most cases it also includes an attachment. NEVER open the attachment on all emails that looks suspicious.
Few tips and signs that an email is fraud and is baiting you into stealing your information:
- Always pay attention to the Sender's address.
- Suppose the sender address looks to be correct. Double-check the spelling, especially if it is asking you about some weird or unusual request. Never respond to the same email.
- They will instruct you NOT to call them. – Then you should definitely call them! Call the number from the company directory or from official sources.
- Too good to be true - "You won the lottery! Hooray!".
- Generic Salutations - Uses "Dear FULL NAME", "GOOD DAY CUSTOMER"
- Contains suspicious attachments that are related to receipts or financial information.
- Poor Grammar - Official emails are well written
- Sense of Urgency - "Your account has been hacked." Microsoft or other vendors will never email you asking for your personal information. Never give out your passwords.
Another type of Phishing email, more dangerous and targeted – SPEAR Phishing
SPEAR Phishing is like a regular Phishing email. However, it is targeted at a specific user and uses a more complex approach.
Here is an example of how SPEAR Phishing usually looks like.
This time it was “Bob Newby” sending Money transfer details to his colleague Steve Harrington.
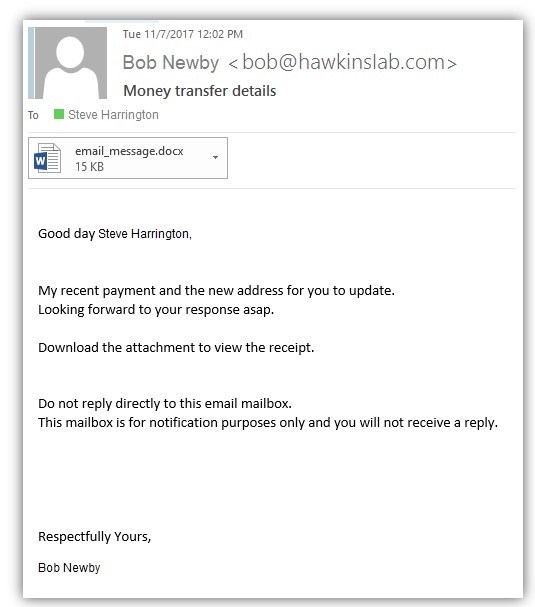
This email looks very real. It also includes an attachment for Steve to download.
But take a closer look at the sender's address again.
![]()
It says the email was bob@hawkinsIab.com, but in fact, the correct business email of Bob would be bob@hawkinslab.com. You thought this was correct, right?
If you type an upper case “i,” it will almost be identical to a lower case “L” on most fonts. It’s really sneaky, so trust your instincts or follow the steps mentioned in this article.
Steve, believing it was Bob opened the attachment.
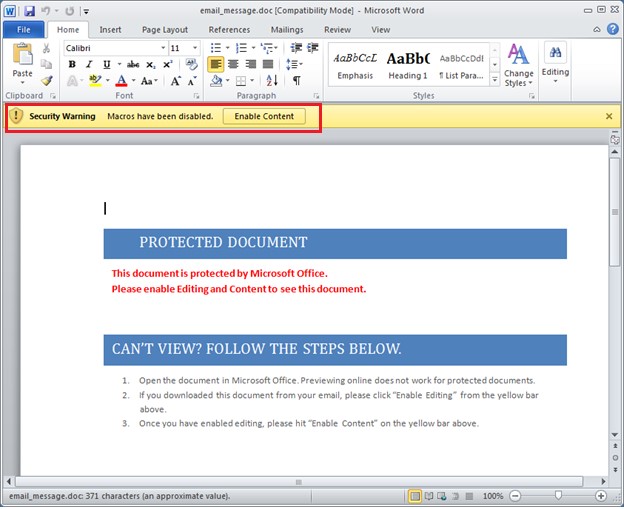
Microsoft Office prevents you from opening these types of documents by default.
The malicious document will contain steps to view the document by clicking the Security Warning button “Enable Content” above. Stop right there soon as you see that Security Warning.
Clicking Enable will execute the payload. It may steal your information and lock you out of the computer.
Please get in touch with Clear Concepts whenever you see a suspicious attachment that asks you to click “Enable Content.” If, for some reason, you accidentally clicked “Enable Content” or the attachment did not prompt you at all. Please call us immediately.
If you can identify that it was a Fake and another Phishing email, IGNORE and report it to Clear Concepts. You will be safe with just leaving it in your Junk or Inbox as long as you never did any of the following.
- Replied to the sender
- Click links from the email
- Open an attachment
Here are some possible combinations of domain impersonation that an attacker could register and use. Take note. We used a company called Hawkins Laboratory here as an example. This could happen to your business name as well.
someone@hawkins-lab.com
someone@hawkinslabs.com
someone@hawkinsIab.com - Iab uses an upper case “i” to make it look like a lower case “L” in some fonts.
someone@hawkinlab.com
More combinations can be used.
What can you do if someone actually copied your domain name?
Contact Clear Concepts and provide a copy of the Phishing email. We will submit a report on your behalf to deactivate the impersonating domain and block the attacker from further sending Phishing emails.
Another tricky situation is when you are expecting an email from a specific sender. Analyze the content of the email and check if that email is legitimate or not. Trust your instincts again.
You can also consider sending an email to your customers and warn them of Phishing emails that may come from someone pretending to be from your organization.
Clear Concepts would be more than happy to provide security recommendations to your customers.
Stranger things happen every day on the internet. It pays to be aware and prepared especially when receiving suspicious emails.
If you have the slightest doubt, stop and don’t follow the instructions from the email.
Call Clear Concepts or forward a copy of the Phishing email to support@clearconcepts.ca, and we will block them from sending emails to other people within your organization.









