Know more about the MFA bombing tactic
Many of us already know the importance of having Multi-Factor Authentication or MFA. Enabling MFA gives many users peace of mind against stolen credentials.
MFA is becoming a standard across many organizations. Over the years, it has spawned different forms based on user or organization preference.
A popular MFA form is the push notification using a mobile authenticator app.
This method added convenience when authenticating to an application. Users only need to tap the MFA notification on their mobile phones to complete or deny the login.
Push notification is probably one of the most convenient but is also one of the weaker forms of MFA.
What is MFA bombing?
MFA bombing is a tactic where the threat actors can send multiple MFA notifications to the target mobile device. This happens if they already gained the password but is still prohibited unless MFA allows the login.
There is a good chance that the victim can get confused about the unexpected notifications and accidentally tap approve, effectively granting access to the threat actors.
What is a better method?
Indeed, adding MFA adds an extra step for everyone. It takes some time to get used to it.
Push notification tap to approve has become one of the popular choices since it is faster and more convenient than the other forms of MFA.
But now, there is another convenient method called number matching MFA as seen in this image:
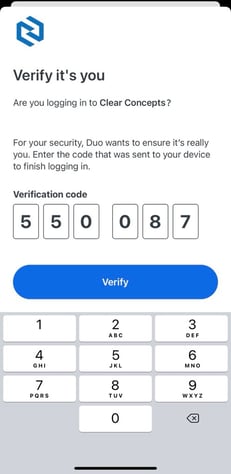
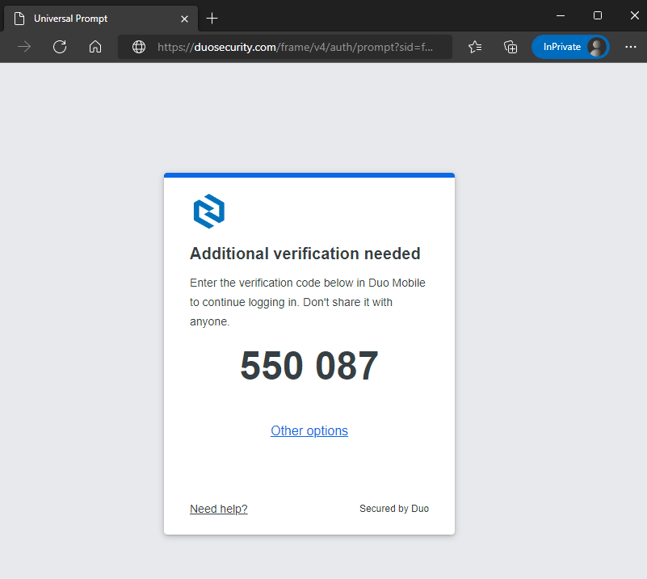
The authenticator app will require the user to match the number displayed on the login screen with their mobile authenticator app. The numbers displayed on the screen and the mobile authenticator app must match before granting access.
Reminder
If anyone experienced the MFA bombing tactic or received an unexpected prompt from their authenticator app, please report it to your IT department as soon as possible.
Also, consider switching to number matching or token-based methods if you still use push notification MFA.
Contact Clear Concepts if you need assistance with implementing Number Matching or Token-Based MFA methods.

